Introduction to Caesar Cryptography
In the realm of cryptography, the Caesar cipher holds a significant place as one of the earliest and simplest forms of encryption. Named after Julius Caesar, who is believed to have used this cipher to protect his military communications, the Caesar cipher exemplifies the foundational principles of cryptographic techniques. This article delves into the intricacies of Caesar cryptography, exploring its mechanism, historical significance, applications, and modern relevance.
What is Caesar Cryptography?
Caesar cryptography involves a substitution cipher where each letter in the plaintext is shifted a certain number of places down or up the alphabet. For instance, with a shift of 3, ‘A’ would be replaced by ‘D’, ‘B’ would become ‘E’, and so on. The Caesar cipher is a type of monoalphabetic cipher, meaning it uses fixed substitution over the entire plaintext.
Key Features of Caesar Cryptography
1. Simplicity and Ease of Use
The primary appeal of the Caesar cipher lies in its simplicity. It is easy to understand and implement, making it an ideal introduction to the concepts of encryption and decryption. The cipher requires minimal computational power, which was especially advantageous in ancient times.
2. Limited Key Space
The Caesar cipher has a limited key space, as there are only 25 possible shifts (ignoring the zero shift, which would leave the plaintext unchanged). This limited key space makes it vulnerable to brute-force attacks, where an attacker could simply try all possible shifts to decrypt the message.
3. Historical Significance
Julius Caesar used this cipher to encrypt his private correspondence, which underscores its historical significance. The cipher’s simplicity allowed for secure communication in an era without sophisticated computational tools, showcasing the early human ingenuity in safeguarding information.
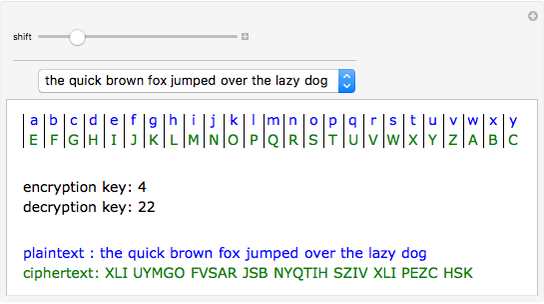
How the Caesar Cipher Works
Encryption Process
To encrypt a message using the Caesar cipher, each letter of the plaintext is shifted a fixed number of positions down the alphabet. For example, with a shift of 3:
- Plaintext: HELLO
- Shift: 3
- Ciphertext: KHOOR
Decryption Process
To decrypt a message, the process is reversed. Each letter of the ciphertext is shifted back by the same fixed number of positions:
- Ciphertext: KHOOR
- Shift: -3
- Plaintext: HELLO
Mathematical Representation
The Caesar cipher can be mathematically represented using modular arithmetic. If ‘P’ is the position of a letter in the alphabet (with A = 0, B = 1, …, Z = 25) and ‘K’ is the shift:
- Encryption: C=(P+K)mod 26C = (P + K) \mod 26C=(P+K)mod26
- Decryption: P=(C−K)mod 26P = (C – K) \mod 26P=(C−K)mod26
Applications of Caesar Cryptography
1. Educational Tool
The Caesar cipher is widely used as an educational tool to introduce students to the basics of cryptography. Its simplicity allows learners to grasp fundamental concepts such as encryption, decryption, and key management.
2. Puzzles and Games
Caesar ciphers are commonly found in puzzles and games. They provide a fun and engaging way for enthusiasts to test their problem-solving skills and understanding of basic cryptographic principles.
3. Historical Research
Historians and cryptographers study the Caesar cipher to gain insights into the early methods of secure communication. Understanding how ancient civilizations protected their information can inform modern cryptographic practices.
Limitations of Caesar Cryptography
1. Vulnerability to Brute-Force Attacks
Due to its limited key space, the Caesar cipher is highly susceptible to brute-force attacks. An attacker can easily try all possible shifts (25 in total) to decipher the message.
2. Lack of Complexity
The simplicity that makes the Caesar cipher accessible also limits its security. It does not provide sufficient complexity to withstand modern cryptographic analysis and is not suitable for securing sensitive information in contemporary applications.
3. Predictability
Since the shift value is fixed, patterns in the plaintext can be easily detected in the ciphertext. This predictability makes the Caesar cipher vulnerable to frequency analysis, where the frequency of letters in the ciphertext is compared to the typical frequency of letters in the language of the plaintext.
Modern Relevance of Caesar Cryptography
While the Caesar cipher is not used for serious cryptographic applications today, it remains relevant as a pedagogical tool and a historical artifact. Understanding the Caesar cipher provides a foundation for learning more advanced cryptographic techniques and appreciating the evolution of secure communication methods.
1. Foundation for Advanced Techniques
The principles underlying the Caesar cipher are foundational to modern cryptography. Techniques such as substitution and modular arithmetic are still used, albeit in more complex forms. Learning about the Caesar cipher helps build a conceptual framework for understanding more sophisticated encryption methods.
2. Cryptographic Awareness
In an age where digital security is paramount, awareness of basic cryptographic techniques, even outdated ones like the Caesar cipher, contributes to a broader understanding of how information can be protected. This awareness is crucial for both cybersecurity professionals and the general public.
3. Cultural and Historical Significance
The Caesar cipher’s enduring presence in popular culture, education, and historical studies highlights its cultural and historical significance. It serves as a reminder of the continuous quest for secure communication throughout human history.
Conclusion
The Caesar cipher is a remarkable example of early cryptographic ingenuity. Its simplicity, historical importance, and educational value make it a subject worth exploring. While it may no longer provide adequate security in today’s digital world, the Caesar cipher’s principles continue to inform and inspire the field of cryptography.



